SELinux 101 : SELinux roles and policies.
SElinux gives applications just enough privileges to be able to run.
In a Linux "traditional" security system, application that need privileged access run as "root", in SELinux, privileged applications run with "customized" rights that exactly fit their need.
SELinux policy:
SELinux uses rules to allow or forbid operations on a system. Each set of rules is called a policy.
SELinux comes with some pre-set policies : targeted and strict.
Strict policy:
It is a policy where everything is denied by default, if anything needs to be allowed, it is done through policy rules.
Targeted policy:
Its is a policy where everything is allowed by default. Processes run
unrestrained using the traditional DAC (Discretionay Access Control) Linux system.
Targeted processes (the ones we apply the rules to) transition after they start into a more restricted execution environment according to the rules of SELinux policies.
Labels or security contexts:
Labels get assigned to different objects (files, processes, sockets,...), they inform SELinux about the rights that need to be granted to each one of these objects.
In the diagram below, we have:
- One-to-one relationship between the Linux user and The SELinux user.
- One-to-many relationship between the SELinux user and The SELinux roles.
- one-to-one relationship between the SELinux roles and The SELinux domains/types.
- have one or more roles, they can transition between roles either automatically following SELinux policy rules or they can do it manually.
- roles determine the types or domains which dictate what is allowed and what is not.
Labels or security contexts for files:
For the files, labels give us an idea about the file's location and function, for example "boot_t" , "kernel_t" or "sshd_t".
The security contexts related to files are stored in the below directory:
/etc/selinux/targeted/contexts/files
"targeted" because it is the existing default policy on a lot of Linux system.
Security contexts for processes:
What a process can do is based on its security context which depends on the identity of the user who started it.
The rights vary depending on the type of objects they apply to (files, directories, sockets,...).
Transition between types:
A SElinux user can have one or multiple roles, automatic transition between roles are handled by the SELinux rules, in order to manually change the roles, we can use the below command:user_u: default SELinux user.
system_u: default user for processes that run at boot time.
Automatic changes of roles occur if they are allowed in the SELinux policy rules.
Exceptions to the automatic domain assignment:
By default a program gets its domain based on the user who started
it.
Key programs (that need privileged access) will switch automatically to a different context after they start so they can get the required privileges of the new domain to be able to run properly.
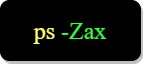
To display the context of the processes in the system we use:
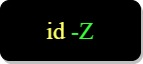
When a user logs in it gets assigned a SELinux user identity, we can display it using:
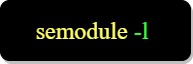
Displaying the SELinux users, roles and types:


















Comments