Docker 101 : Running a container with non-Root (non-privileged) user in Docker and Kubernetes
Running a container with non-root user:
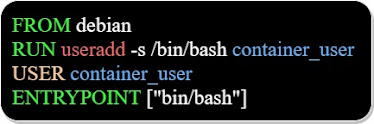
To be able to run a container with a non-root user, we build the docker image, mentioning the user that the image will later use to run the container, as we can see in the below Dockerfile:
All the commands below the "USER container_user" instruction run under the "container_user" id.
We can run the image in a container using the below:
Kubernetes pods and non-privileged users:
If we are using kubernetes, we could override the fact that the container runs with a root user, by creating a "non-privileged" user for the pod in which the container "lives" ( ID: 6500 -mentioned below- ).
All the containers in the "secure-pod" will run under the user mentioned in "runAsUser".
The "runAsGroup" performs the same function for the user group.














Comments