Security 101 : Access Control Lists (ACL)
Access Control Lists (ACL):
In Unix, file permissions are as follows:
- Access rights for the owner of the file.
- Access rights for the group the file belongs to.
- Access rights for the rest of the users that are not members of the group the file is associated to.
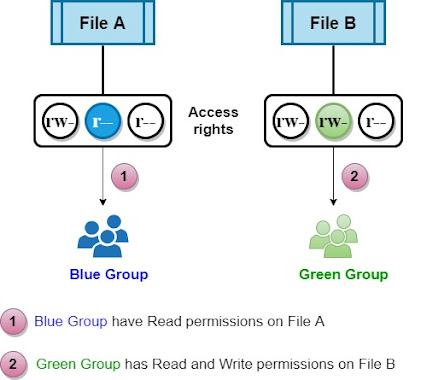
Group permissions:
The above system presents certain limitations.
Group permissions help us grant different access rights to different groups of users, but a file can only belong to one group.
When we want to associate a file with a different group of users with different access rights, a new group needs to be created.
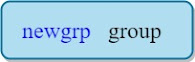
A user can switch to a different group he is member of using the command:
The standard Unix access model doesn't lend itself easily to cases where a file for example needs to be "read-only" by one group of users and "readable, writable" by another group of users.
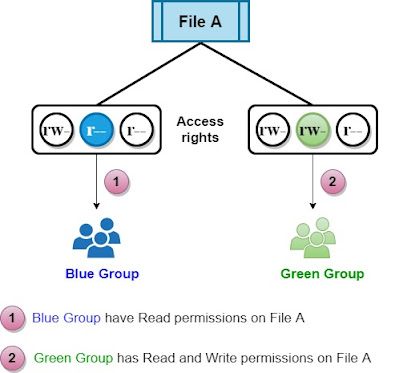
File permissions could be seen as a simple form of the access control list (ACL).
ACL permissions apply to all the objects in the filesystem (files, directories,...).
UFS FreeBSD filesystem and ZFS filesystem support ACLs.
NFSv4 ACL:
ACLs allow us to have more control over access rights.
We could have different users and different groups with different access rights to the same file for example.
Example:
Remark:
NFSv4 ACL allows the ACL permissions to be shared over the network.
Mounting File Systems:
In order to use ACL on a file, the partition that holds the file must have ACL support.
To be able to do so we mount the filesystem with ACL support.
Example:
Mounts the partition /dev/sd2 with ACL support on the mountpoint /home/Albert directory.
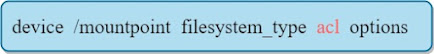
we can also add the ACL support in the /etc/fstab file:
NFS and the no_acl option:
We can use the "no_acl" option in the /etc/exports file to disable ACL for an NFS mount.
ACL types:
Access ACLs : applicable to files and directories.
Default ACL: only applicable to directories.
Remark:
A file without ACL in a directory with default ACL "inherits" the ACL of the directory.
How to configure ACLs (setfacl command):
The setfacl sets the ACLs for files and directories:
Options:
-m : to add or modify the ACL.
-x : To remove permissions.
Rules :
we can have multiple rules separated by a comma for example.
- u:uid:perm : Sets the ACL for a user (username or UID could be used).
- g:gid:perm : Sets the ACL for a group (The group name or GID could be used).
- o:perm : sets the access ACL for the rest users.
- m:perm : Sets ACL mask, it used to give default permission to newly created folders and files.
Perm could be read-only (r--) or read-write (rw-) for example.
Setting the ACL mask:
we can set the mask using:
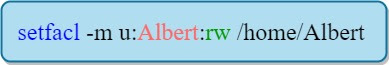
Example:
In order to give read and write permissions to the user Albert on /home/Albert :
Removing ACL permissions:
To remove all the permissions for a user, group, or others, use the -x option:
Example:
To remove all the permissions from the user with UID 900:
Default ACLs:
To set a default ACL, add "d:" before the rule and specify the directory.
For example, to set the default ACL for the /home directory to -read-execute- for other users not in the user group, we do the following:
Remark:
Access ACL for an individual files can override the default ACL for the directory that contains it.
Displaying ACLs:
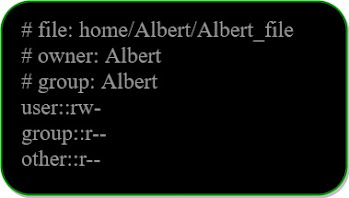
We use the getfacl command to retrieve the ACLs.
Example:
We get the below output:
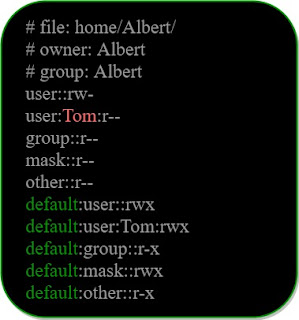
If a directory has default ACL , the default ACL are also displayed
Remark:
We also have a user "Tom" with read rights.






















Comments