Linux 101 : SSH (The Secure Shell) - scp, ssh-keygen -
When the client starts a connection with the server, the client should be able to verify that it is connecting to the "right" server.
The server accept connections only from trusted clients and the exchange of data between the client and the server needs to be encrypted.
The trust relationship between the client and the server is done through the SSH encryption keys.
SSH Encryption Keys:
Asymmetric encryption keys are made up of a public key and a private key.
The private key is never sent over the network.
The public key is sent to host that needs to send encrypted data.
The host encryption key: is configured once for each SSH server and stored in a local file. The below files are created when the "sshd" daemon is launched for the first time:
Session Keys:
The user encryption key (details):
The server accept connections only from trusted clients and the exchange of data between the client and the server needs to be encrypted.
The trust relationship between the client and the server is done through the SSH encryption keys.
SSH Encryption Keys:
Asymmetric encryption keys are made up of a public key and a private key.
The private key is never sent over the network.
The public key is sent to host that needs to send encrypted data.
Types of encryption keys:
The host encryption key: is configured once for each SSH server and stored in a local file. The below files are created when the "sshd" daemon is launched for the first time:
The user encryption key:
It is composed of a private and a public key, these keys are stored in two files in the the ".ssh" directory below the user "home" directory.
The public key is then copied on the server authorized_keys file, this is how the server can trust the user "User".
Session Keys:
After the client/server trust relationship is established through the encryption keys, they set the session encryption key.
This key is used for one session between the client and the server to encrypt the sent data.
This key is used for one session between the client and the server to encrypt the sent data.
These keys are generated automatically.
The user encryption key (details):
SSH connections need a password to allow the users to connect to a remote SSH server.
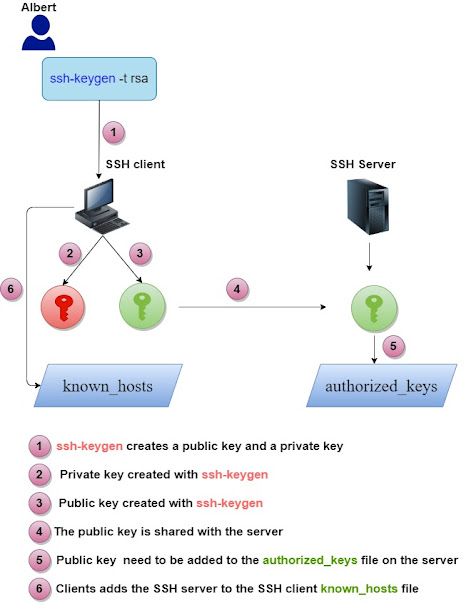
To be able to connect to a remote server without being prompted for a password, keys need to be generated for each user.
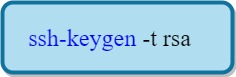
The user types the below command to generate the "user" keys:
Remark:
We do not use a passphrase (leave blank) so we don't get prompted to enter it each time it the connection to the server takes place.
The public encryption key is now stored in :
We copy the Public Encryption Key stored in the file id_rsa.pub From the SSH Client to authorized_keys file on the SSH Server.
On the SSH server we do the following, if the .ssh directory does not exist for the user "User":
On the SSH server we do the following, if the .ssh directory does not exist for the user "User":
We paste in the public key of the user in the file authorized_keys on the SSH server:
This file contains a list of authorized client's public keys. The server can check if the client has the right to connect to it by looking up its public key stored in this file.
We change the attributes of the file to keep other users from modifying the file:
Example:
known_hosts file : SSH clients keep the keys for the servers they have connected to in the file /home/user/known_hosts. That ensures that the SSH client is connecting the right SSH server.
Connecting as root:
The scp command:
The scp command can be used to transfer files securely between machines :
Example:
This will transfer the local file "file1" to "/home/Albert/file2" on the host "11.1.10.22".
Removing stale entries (known_hosts file):
To remove a host's data from the "known_hosts" file, we use:
























Comments