Docker 101 : Communicating with containers from inside and outside the host machine
Each container is created in its own network namespace, and docker uses virtual network cables called veth to connect these network namespace through the virtual bridge called docker0, which is the default switch docker uses to connect its containers.
The eth0 interface of the container is connected to the virtual bridge/switch using the veth virtual cable.
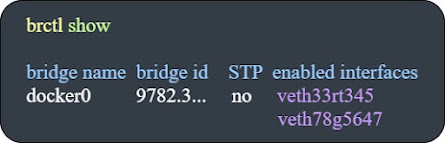
To display the Linux bridges on the host, we could use the below command:
Show the virtual bridge and the veth interfaces that connect it to the containers.
To be able to reach the containers from the outside, iptables are used for masquerading the IP addresses.
The hosts changes the container's IP address in the outgoing packets with its address and does the opposite for the incoming packets.
Below we could see and example of the masquerading rules in iptables:
Masquerading happens for all the packets with a source IP address in the "172.17.0.0/16" range and external destination IP address.
Remark:
POSTROUTING happens when a packet is about to leave the network interface.
below we can see the docker0 bridge represented in Linux as a network interface:
below we can see the docker0 bridge represented in Linux as a network interface:
Remark:
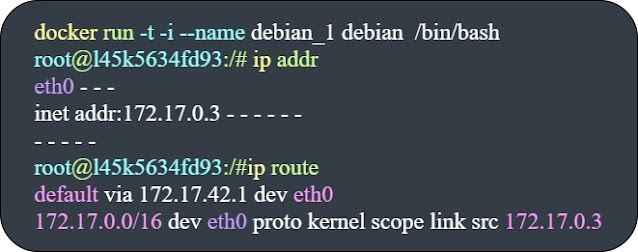
Docker uses the docker0 bridge IP address range to assign IP addresses to its containers when they are created using the below command for example:
We can see from the above output, the container's network interface and its routing table.
Remark:
The docker0 bridge gets by default the IP address "172.17.42.1", and docker gives its containers IP addresses in the "172.17.0.0/16" range.














Comments