Linux 101 : Basic port scan using Netcat
According to the TCP protocol, a full connection is when a three-way handshake is established.
The below diagram illustrates that mechanism:
The three-way handshake so the two hosts can agree on the different parameters of a TCP connection before sending any data.
As we can see in the above diagram the "computer A" sends a SYN packet to the "Server A" on a specific port.
If the port is open, "Server A" sends a SYN-ACK packet, then the "Computer A" sends an ACK packet, after that step the connection is established.
A full connection involving a three-way handshake to connect to a remote port - as described above - can be achieved using the netcat tool.
The below command scans a wide range of ports - 2500-2600 - for the host - 10.20.15.22 -, using netcat:
Below is a short description of the above parameters:
- -w : is the connection timeout window in seconds.
- -n : tells netcat not to perform any DNS lookups - use only IPs -.
- -v : verbose mode, to display more information that usual.
- -z : tells netcat that no data will be sent over this connection - that it is only for scanning purposes -.
The UDP protocol on the other hand doesn't save any data about its state - it is stateless -, there is no three-way handshake involved.
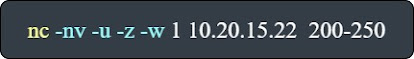
To perform a scan on the UDP ports - 200-250 - of a machine - 10.20.15.22 - , we use the below command:
- -u : tells netcat that its a UDP scan.













Comments