Kubernetes 101 : Securing our docker images - Private docker registry, Custom applications -
The complete name is of the image: "docker.io/library/nginx"
- library: is default account name, if none is provided - it is the official docker account - .
- nginx: is the image name
- docker.io: is the default location for the image, if none is provided
To host our own images, we will use our own account and location - registry -, for example "company_name.io/company_name".
To host "private" images, we could use a private registry that will be accessible through a username and password for example.
To pull an image from a private registry, we need to login first using the below command:
After entering the username and the password, we could use our "private" image as below for example:
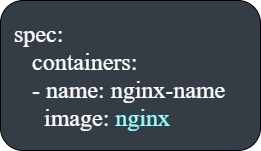
To use a private image in kubernetes, we provide our pod's Yaml file with the full path to our application:
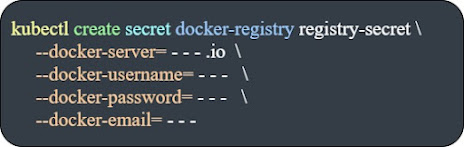
To be able to manage the authentication as a part of the pod's configuration, we create a kubernetes secret that has a "docker-registry" type.
This type of secrets is used to keep docker logins and passwords.
We create our secret using the below command:
Now, we can use our private image as shown below, the secret object is mentioned in the imagePullSecrets parameter:















Comments