Security 101 : Nmap - Basic commands -
The nmap tool:
The nmap tool allows us, among other things, to do a UDP or TCP scan of the network ports on a network of hosts.
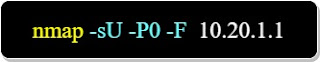
-P0 : assumes that the host is up but not responsive to host discovery (Ping scan).
-F : fast scan to a limited number of ports.
The above command scans a range of UDP ( 51 to 118 ) and TCP ( 80 to 137 ) ports.
-O : checks the operating system.
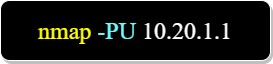
-PS : does a TCP port scan.
Aggressive mode:
Remark:
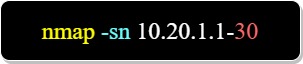
Scanning a limited number of hosts in a network:
The example below scans 30 hosts in the network "10.20.1.0":
Using the above command, nmap pings each host to see if the host is up.
Limiting the number of scanned hosts using the network mask:
Using the network mask, we can limit the number of hosts scanned:
The whole address is 32 bits. If we use 24 bits for the network mask, we will be left with 8 bits for the hosts.
The 8 bits represent hosts from address 10.10.20.1 to address 10.10.20.254 ( 1+2+4+...+128 = 255).
The 10.10.20.255 is a special address dedicated to broadcasting.
The above command scans hosts from 10.20.1.1 to 10.20.1.254.
-sn : only performs a host discovery.
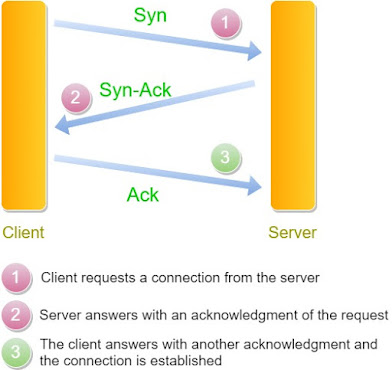
TCP SYN ping scan:
We can use the above command to check if any service is open on the host.
The command opens a connection on the port of a service and closes it before the connection is fully established (TCP SYN ping).
We send an empty TCP packet with a SYN flag set and we wait for the usual SYN ACK response
UDP ping scan:
We could also use UDP scan, that by default it scans the port 40125 which is not likely to be used.
The "port unreachable" response indicates the the host is up.
Below is the command for the UDP scan:
Scanning and version discovery:
The above command displays the version of the service running on port 80.
UDP scanning:
-P0 : assumes that the host is up but not responsive to host discovery (Ping scan).
-F : fast scan to a limited number of ports.
-sU : does a UDP port scan.
The above command displays a list of UDP ports and the services associated with them.
Scanning port ranges :
-sSU : scans both TCP (T) and UDP (U) ports.
The above command scans a range of UDP ( 51 to 118 ) and TCP ( 80 to 137 ) ports.
Discovering the operating system of a host:
-O : checks the operating system.
-PS : does a TCP port scan.
Aggressive mode:
The above command probes the TCP ports and a does a host discovery ( Ping scan ).
-PS : does a TCP port scan (Ping Scan)
-A : Aggressive mode which does OS detection (-O), software version detection (-sV), script scanning (-sC) and "traceroute" which records information about the route the packets take on their way to their destination (10.20.1.1).
-A : Aggressive mode which does OS detection (-O), software version detection (-sV), script scanning (-sC) and "traceroute" which records information about the route the packets take on their way to their destination (10.20.1.1).
Remark:
-s : stands for a script scan, it uses the default nmap scripts.


















Comments