Kubernetes Security 101 : RBAC roles ( Role-Based Access Control ) and Role bindings
When we have users to whom we want to give similar access rights, we attach them to the same role.
Each role has a set of access rights, so instead of giving the same access rights to each of the "similar" users, we give the access rights to a role and attach all the "similar" users to it.
Creating a role:
We could have roles for database administrators, developers,...
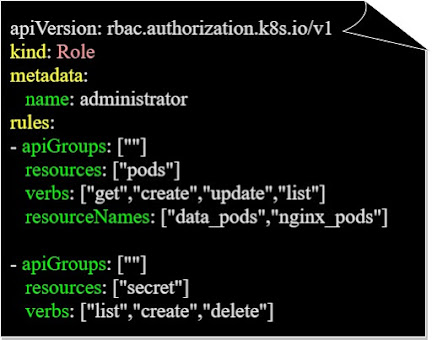
We create a role by creating a kubernetes resources in a Yaml format "administrator-role.yaml":
We create a role by creating a kubernetes resources in a Yaml format "administrator-role.yaml":
- The apiGoups is blank, because the "role" resource belongs to one of the the main API groups
- The verbs represents the allowed actions for the role.
- The resourceNames are the name of the resource "data_pods" and "nginx_pods" in the above example, that the user can apply the "verbs" to.
We create a role using the below command:
We can have multiple rules for a role.
Role binding:
To attach a role to a user, we will need to write a RoleBinding resource in a Yaml format:
Then we can create the RoleBinding resource, that binds the user "admin" to the role "administrator", using the below command:
Roles are namespaced, if we don't mention a namespace in the Yaml configuration file, they will be created in the default namespace.
We can limit a user to a certain namespace by adding the namespace name in the Yaml configuration file.
Displaying the role:
We can display the roles in a cluster using the below command:
Displaying the role binding:
We display the role binding resources in a cluster using the below command:
Displaying information about a role:
To get more information about a role, we could use the below command to get more information about the administrator role:
Displaying the rights of users:
To see our access rights as a user, we could use the below command to see our rights regarding the creation of "pods" for example:
We could optionally add the namespace to see the rights in that specific namespaces:
Displaying kubernetes namespaced resources:
To display the kubernetes resources that are namespaced (that live in namespaces), we use the below command:






















Comments